The pace of technology is only speeding up, and so are the tactics used by online abusers. Which is why M3AAWG is excited to share important updates on how the organization is focusing its work moving forward.
With the help of our members, we’ve identified a new set of Priorities and Focus Areas that reflect both where the abuse is happening today and where it's headed. These updates are proactive, clear, and aligned with the real-world challenges our community is working to solve and prevent every day.
"A future of technological change brings unprecedented challenges for the anti-abuse community,” said Amy Cadagin, M3AAWG Executive Director. “M3AAWG is nimble, and our success has always hinged on our ability to identify online threats and proactively develop industry best practices to make the internet a safer place for all. We’re proud to announce this evolved set of priorities and focus areas that underscore the direction of our collective expertise and resources.”
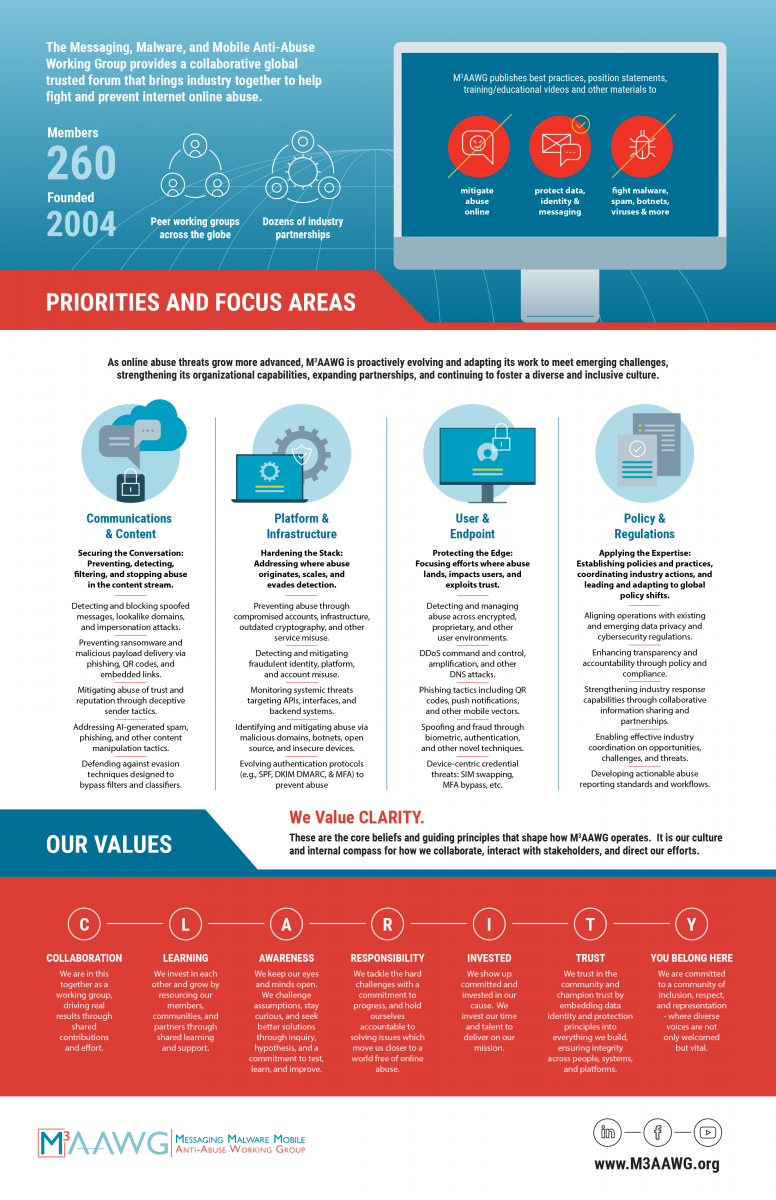
Four New Priorities to Maximize our Impact
M3AAWG has identified four organizational priorities to ensure it remains laser-focused toward achieving a world free of online abuse:
- Communications & Content. Securing the Conversation: Preventing, detecting, filtering, and stopping abuse in the content stream. Example Focus Areas:
- Detecting and blocking spoofed messages, lookalike domains, and impersonation attacks.
- Preventing ransomware and malicious payload delivery via phishing, QR codes, and embedded links.
- Mitigating abuse of trust and reputation through deceptive sender tactics.
- Addressing AI-generated spam, phishing, and other content manipulation tactics.
- Defending against evasion techniques designed to bypass filters and classifiers.
- Platform & Infrastructure. Hardening the Stack: Addressing where abuse originates, scales, and evades detection. Example Focus Areas:
- Preventing abuse through compromised accounts, infrastructure, outdated cryptography, and other service misuse.
- Detecting and mitigating fraudulent identity, platform, and account misuse.
- Monitoring systemic threats targeting APIs, interfaces, and backend systems.
- Identifying and mitigating abuse via malicious domains, botnets, open source, and insecure devices.
- Evolving authentication protocols (e.g., SPF, DKIM DMARC, & MFA) to prevent abuse.
- User & Endpoint. Protecting the Edge: Focusing efforts where abuse lands, impacts users, and exploits trust. Example Focus Areas:
- Detecting and managing abuse across encrypted, proprietary, and other user environments.
- DDoS command and control, amplification, and other DNS attacks.
- Phishing tactics including QR codes, push notifications, and other mobile vectors.
- Spoofing and fraud through biometric, authentication, and other novel techniques.
- Device-centric credential threats: SIM swapping, MFA bypass, etc.
- Policy & Regulations. Applying the Expertise: Establishing policies and practices, coordinating industry actions, and leading and adapting to global policy shifts. Example Focus Areas:
- Aligning operations with existing and emerging data privacy and cybersecurity regulations.
- Enhancing transparency and accountability through policy and compliance.
- Strengthening industry response capabilities through collaborative information sharing and partnerships.
- Enabling effective industry coordination on opportunities, challenges, and threats.
- Developing actionable abuse reporting standards and workflows.
"These priorities replace and evolve our previous model. Through our collective efforts, our leadership and officers have worked to make these priorities clearer, more actionable, and better aligned with how abuse actually operates across systems, people, and platforms," said Sara Roper, Chairperson of the M3AAWG Board of Directors.
We Value CLARITY
M3AAWG’s values serve as its cultural identity and act as an internal compass for collaboration, stakeholder interaction, and the allocation of resources and efforts. Alongside these new priorities and focus areas, M3AAWG has identified seven key principles that embody the “CLARITY” of its values:
C-OLLABORATION. We are in this together as a working group driving real results through shared contributions and effort.
L-EARNING. We invest in each other and grow by resourcing our members, communities, and partners through shared learning and support.
A-WARENESS. We keep our eyes and minds open. We challenge assumptions, stay curious, and seek better solutions through inquiry, hypothesis, and a commitment to test, learn, and improve.
R-ESPONSIBILITY. We tackle the hard challenges with a commitment to progress, and hold ourselves accountable to solving issues which move us closer to a world free of online abuse.
I-NVESTED. We show up committed and invested in our cause. We invest our time and talent to deliver on our mission.
T-RUST. We trust in the community and champion trust by embedding data identity and protection principles into everything we build, ensuring integrity across people, systems, and platforms.
Y-OU BELONG HERE. We are committed to a community of inclusion, respect, and representation - where diverse voices are not only welcomed but vital.
Get Involved
If you are not a M3AAWG member, you can learn more about joining M3AAWG here.
Are you a member who has never attended a meeting? We encourage you to consider attending an upcoming M3AAWG Meeting in person to experience the firsthand connections and collaboration that serve as a hallmark of our organization’s impact.
Additionally, we encourage you to stay tuned to this blog and follow M3AAWG on Facebook and LinkedIn for information about attending our upcoming Engagement Series, which will feature M3AAWG leadership sharing more updates on our strategic direction as we work to stay ahead of emerging threats and evolving abuse tactics.